
A popular WordPress security plugin, WPS Hide Login, was found to have a vulnerability. The issue was promptly patched as soon as it was discovered.
The WordPress Vulnerability Database describes the update like this:
“fixed a vulnerability in version 1.5.4.2 and below that could allow an attacker to find and access the secret login page.”
What Is the WPS Hide Login Vulnerability?
WPS Hide Login is a WordPress plugin that creates a hidden admin login page, which prevents hackers from performing password guessing attacks since the login page is obscured.
The vulnerability allows a hacker to cause the plugin to reveal the URL for the hidden page, enabling an attack.
Versions 1.5.4.2 and Older Affected
This vulnerability affects plugin version 1.5.4.2 and all users are urged to update their plugin to version 1.5.5 immediately.
How the Vulnerability Was Discovered
A web application firewall publisher, NinTechNet, discovered the vulnerability on January 20, 2020. They informed the developers of WPS Hide Login, who addressed and closed the vulnerability the same day.
The publisher later released an account of the discovery after the plugin had been updated.
WPS Hide Login Changelog
Every WordPress plugin logs its updates in a document called a changelog. Web publishers can check the changelog from the WordPress plugin dashboard to determine whether an update is critical.
Some updates can disrupt a site, so some administrators may opt not to update unless it’s for something crucial.
Ideally, software creators should indicate the importance of an update, especially if it addresses a vulnerability.
This update is crucial because the vulnerability undermines the plugin’s primary function: hiding the admin login page.
Is it unreasonable to expect this to be communicated in the changelog?
Here is a screenshot of the changelog for WPS Hide Login:
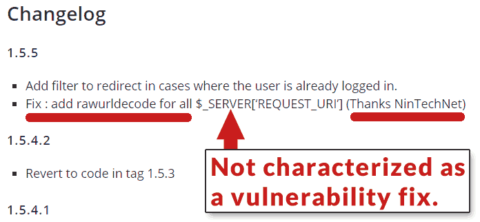
As you can see in the screenshot, there is no mention of what the update addresses or any indication of its importance.
WPS Hide Login Responded Responsibly
WPS Hide Login acted responsibly by quickly patching their plugin. However, it would be beneficial if they also communicated the significance of updates, especially when they involve security vulnerabilities.



