Popular WordPress Plugin Popup Builder has been found to possess multiple vulnerabilities. These issues could enable an attacker to inject malicious JavaScript into a popup.
Vulnerability in Popup Builder Plugin Discovered
The vulnerability was identified by WordFence on March 4, 2020, and they subsequently informed the developers. The affected WordPress plugin versions are those below 3.64.1.
A patched update was uploaded by the plugin developers a week later, on March 11, making the updated plugin available for download.
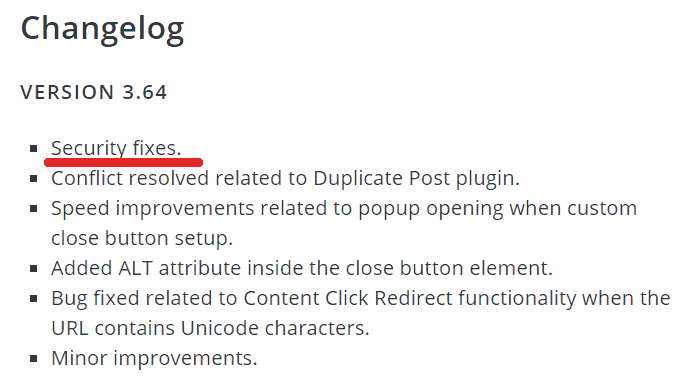
Changelog
A changelog describes what an update entails and is critical for users to understand the urgency of an update. Unfortunately, some WordPress plugin developers either neglect to mention security issues or describe them in vague terms.
Popup Builder plugin’s changelog mentions a security update but does not specify its severity or importance. While it does disclose that the update addresses a security concern, it labels it simply as "Security fixes," a description that lacks urgency given the seriousness of the vulnerability.
Here is a screenshot of Popup Builder’s changelog:
What are the Vulnerabilities?
There are two vulnerabilities. The first one allows an attacker to insert harmful JavaScript into a popup. The second vulnerability permits the attacker to download subscriber lists and access numerous plugin features.
These vulnerabilities affect over 100,000 plugin users. It is essential for publishers to download and update their plugins.
According to WordFence:
"Typically, attackers use a vulnerability like this to redirect site visitors to malvertising sites or steal sensitive information from their browsers, though it could also be used for site takeover if an administrator visited or previewed a page containing the infected popup while logged in."
It is crucial to update this plugin. Not doing so could invite hackers to take over a site.
Read the announcement by WordFence:
Vulnerabilities Patched in Popup Builder Plugin Affecting over 100,000 Sites



