
Redux, a widely used WordPress plugin with over 1 million active installations, recently patched a vulnerability. This flaw allowed an attacker to bypass security measures in a Cross-Site Request Forgery (CSRF) attack.
Cross-Site Request Forgery
A Cross-Site Request Forgery (CSRF) attack is a method where an attacker exploits a vulnerability in the code that allows them to perform actions on a website. This kind of attack exploits the credentials of an authenticated user.
The U.S. Department of Commerce defines CSRF like this:
"A type of Web exploit where an unauthorized party causes commands to be transmitted by a trusted user of a Web site without that user’s knowledge."
This particular attack bypassed security checks by exploiting a coding bug that caused a site to improperly validate security tokens called nonces. Nonces are supposed to protect forms and URLs from such attacks.
The WordPress developer page describes nonces:
"WordPress nonces are one-time use security tokens generated by WordPress to help protect URLs and forms from misuse.
If your theme allows users to submit data; be it in the Admin or the front-end; nonces can be used to verify a user intends to perform an action, and is instrumental in protecting against Cross-Site Request Forgery (CSRF).
The one-time use hash generated by a nonce, prevents this type of forged attacks from being successful by validating the upload request is done by the current logged in user. Nonces are unique only to the current user’s session, so if an attempt is made to log in or out any nonces on the page become invalid."
The flaw was in how the nonces were validated. This vulnerability was originally fixed in October 2020 but was reintroduced in a later update.
According to the WPScan security plugin:
"The plugin did not properly validate some nonces, only checking them if their value was set. As a result, CSRF attacks could still be performed by not submitting the nonce in the request, bypassing the protection they are supposed to provide."
Both WPScan and the WordPress Redux plugin reported that the CSRF vulnerability has been fixed.
WPScan described the current issue:
"The plugin re-introduced a CSRF bypass issue in v4.1.22, as the nonce is only checked if present in the request."
The Redux Plugin changelog states:
"Fixed: CSRF security issue with a flipped if conditional."
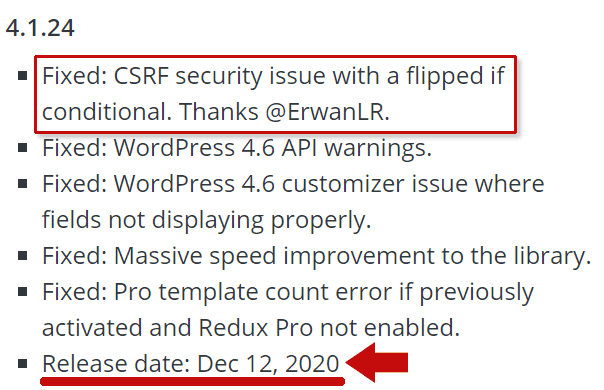
Update Redux Gutenberg Blocks Library & Framework
Redux is a plugin that allows publishers to browse and choose from thousands of Gutenberg blocks and templates. Blocks are sections of a web page, and templates are entire web page designs.
With over a million active users, Redux plugin is one of the most used WordPress plugins. It is highly recommended that publishers using the Redux WordPress plugin immediately update to the latest version, 4.1.24.



